Published on: May 22, 2025
3 min read
Introducing compromised password detection for GitLab.com
GitLab is adding compromised password detection on June 19, 2025. After that date, users logging in with known compromised passwords will be warned. Here is what you need to know.

Data breaches have become more common than ever. According to a recent report by the Identity Theft Resource Center, over 2,800 data breaches occurred in 2024 alone, with over 1 billion victim notices sent by compromised organizations. Often, these breaches result in the exposure of credentials – usernames, emails, and passwords – in plain text, either directly or with insufficient protection against conversion to plain text. These compromised or stolen credentials are actively and widely leveraged by attackers, too. Verizon’s 2024 Data Breach Investigations Report identified use of stolen credentials as the initial action in 24% of breaches, ranking it as their top initial action.
GitLab.com stores your password securely, salted and hashed with bcrypt. Your password goes through a one-way hashing transformation before storage, securing your password and ensuring it is not possible to extract the original password from storage. The representation is also unique: Even if two users shared the same password, the results of the one-way transformations would be completely different. However, these safeguards intentionally make it impractical to identify all users with a compromised or otherwise weak password.
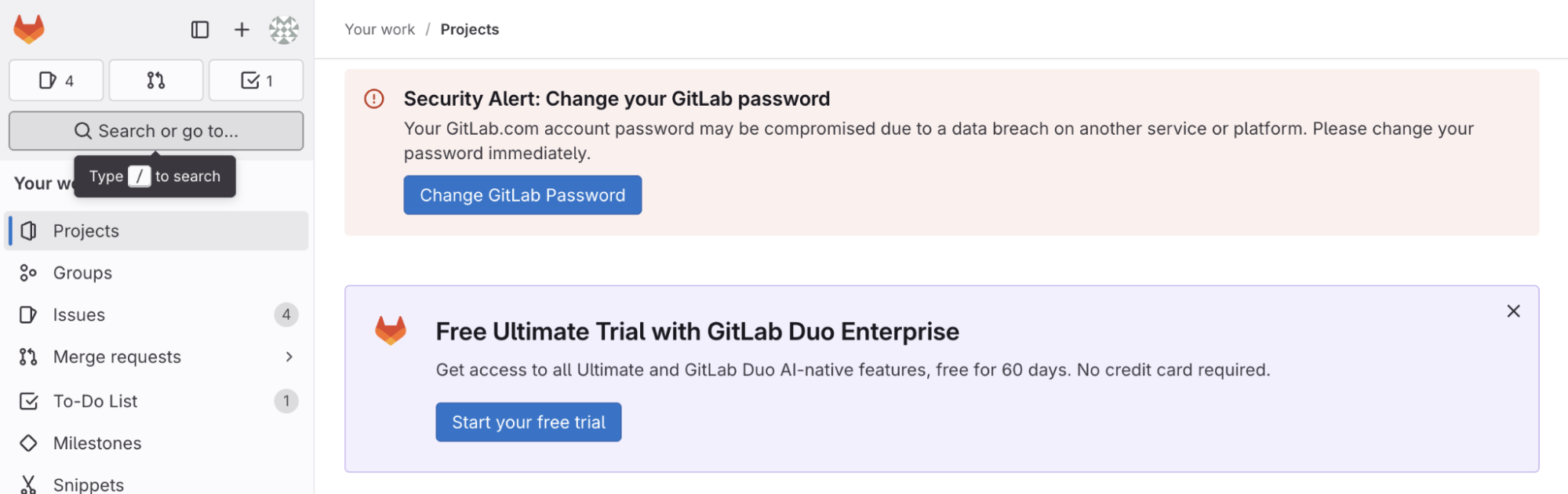
Starting on June 19, 2025, GitLab will be introduce compromised password detection during sign-in for all GitLab.com users. This works by securely comparing the password you log in with against a database of known compromised credentials during authentication. If the password is correct but matches known compromised credentials, you will be alerted with a banner on GitLab.com and you will be sent an email notification until you change your password.
Note: Compromised password detection is only for logins using GitLab’s native username and password and does not apply to credentials used through SSO.
Example compromised password warning banner:
We’re excited to introduce this additional countermeasure to help ensure your account is secure. We also encourage users to take these additional preventive actions to maintain the security of your account(s):
- Use a strong password unique to your GitLab.com account. GitLab disallows weak passwords that are considered compromised or that contain part of your name, email address, or predictable words. We strongly recommend using a password manager like 1Password, Google Password Manager, or Apple Passwords, as well.
- Set up two-factor authentication for your GitLab.com account. GitLab supports time-based, one-time password applications, like Google Authenticator and WebAuthn, with a PIN/fingerprint or a hardware security key.
- Prevent yourself from getting locked out of your account. Change your primary email address if you no longer have access, and ensure you have recovery codes in case your two-factor authentication device is lost or stolen. Also, consider setting up an alternative method for two-factor authentication.
- Stay aware of new risks. Register with a service like haveibeenpwned.com to receive an email notification if your email address appears in a newly disclosed breach. This service is free to use and requires only your email address at registration.
To learn more about trust and security measures on GitLab.com, visit the GitLab security page, highlighting the GitLab Trust Center, compliance certifications, and security measures that keep users and customers safe on our platform.

